Phishing is a form of attack where an intruder tries to coax sensitive data from a victim. It is a common threat that has existed for many years. Phishing uses various social engineering techniques to persuade an unsuspecting user to provide their credentials, which are then collected by the attacker. Recently, a completely new method has emerged that even IT experts may fail to detect.
Despite using all kinds of protection systems, every user using the internet should become vigilant today. When surfing the web, and especially when clicking on links or redirects to other websites, it is advisable to first check if the URL address is correct – i.e. to make sure that you are visiting google.com rather than googlle.com. “A single letter can cause big problems. Both websites may look identical. But only one of them is the original. The other one will quite possibly be a fake website aimed at luring personal data from users through phishing,” says Martin Lohnert, a cybersecurity specialist at Soitron.
After the user has made sure that they are at the correct address, they should also check to see if there is the lock icon in front of the address (the website URL starts with https, which means that the website is secured by TLS/SSL encryption). In this way, the browser notifies the user that communication with the website is secure. These two checks should now be complemented with one more check.
A new phishing technique called the “browser-in-the-browser” (BitB) attack, as described by the penetration tester known as mr.d0x, simulates a pop-up BitB window. This mainly includes a third-party single sign-on (SSO) window.
Currently, it is quite common for people to use their Google, Microsoft, Apple, Facebook, and similar accounts to verify their identity on a website, service, or e-shop. With pop-up windows saying “Log in using…”, they don’t have to create new accounts all the time; however, by imitating this window or other legitimate domain, it is possible to conduct a convincing phishing attack.
When a user attempts to log in using the SSO method, the default behaviour of a web page is to display a pop-up window to complete the authentication process. BitB attacks aim to replicate this process by using a combination of HTML code and CSS styling to create a completely fake identical browser window. “Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and it’s basically indistinguishable from the real window,” writes mr.d0x.
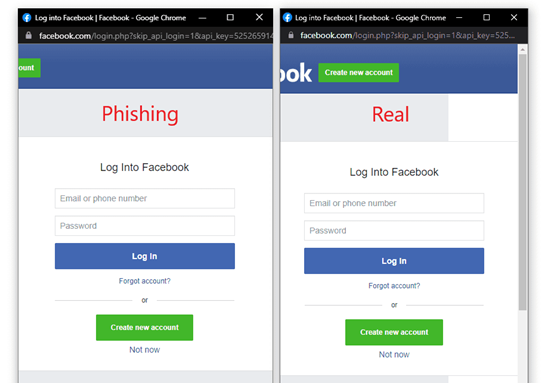
As soon as the user fills in the login details – most often a name, email, or telephone number along with a password – they are in trouble because they have unknowingly revealed their credentials. The data may not be necessarily abused right away; however, it is stored in the attacker’s database, bundled up with other data, and immediately offered for sale. The login data is then exploited by the subsequent buyer.
“In addition to checking the URL to see you are visiting the real website and making sure that the communication is encrypted, another form of protection against this type of attack is to grab the SSO window and try to move it outside the currently loaded web page. If this is possible, then everything is all right. If not, it is a fake JavaScript window. Never put your login details into such a window,” Lohnert concludes.
We are in the process of finalizing. If you want to be redirected to our old version of web site, please click here.